The posture configuration is very similar to the one that was created in the Anyconnect VPN post. This post will go over the posture steps and demonstrate what it looks like on a switch and also in the ISE RADIUS live logs.
On a wired LAN connection using dot1x the ISE posture can determine based off a username if the device is a corporate machine and place them into a corporate VLAN. If the client is unknown, move it to a guest VLAN with a specific ACL, or deny them altogether.
For this lab demonstration, posture results will have the following outcomes;
- Have a default guest VLAN on the switchport
- Guest VLAN will have an ACL that denies traffic to the LAN, except for posture and DHCP/DNS
- If a user is compliant, they will be placed into an employee VLAN
- Users will have an ACL based off their groups
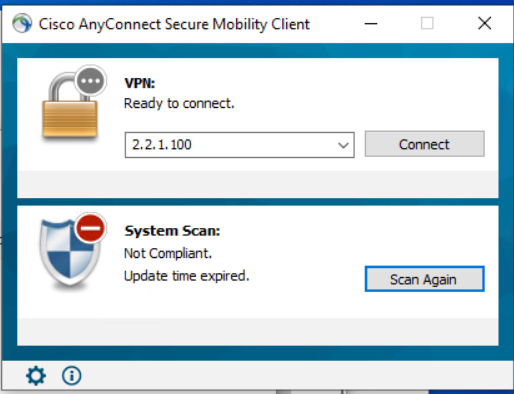
Employee Compliance Posture Fail
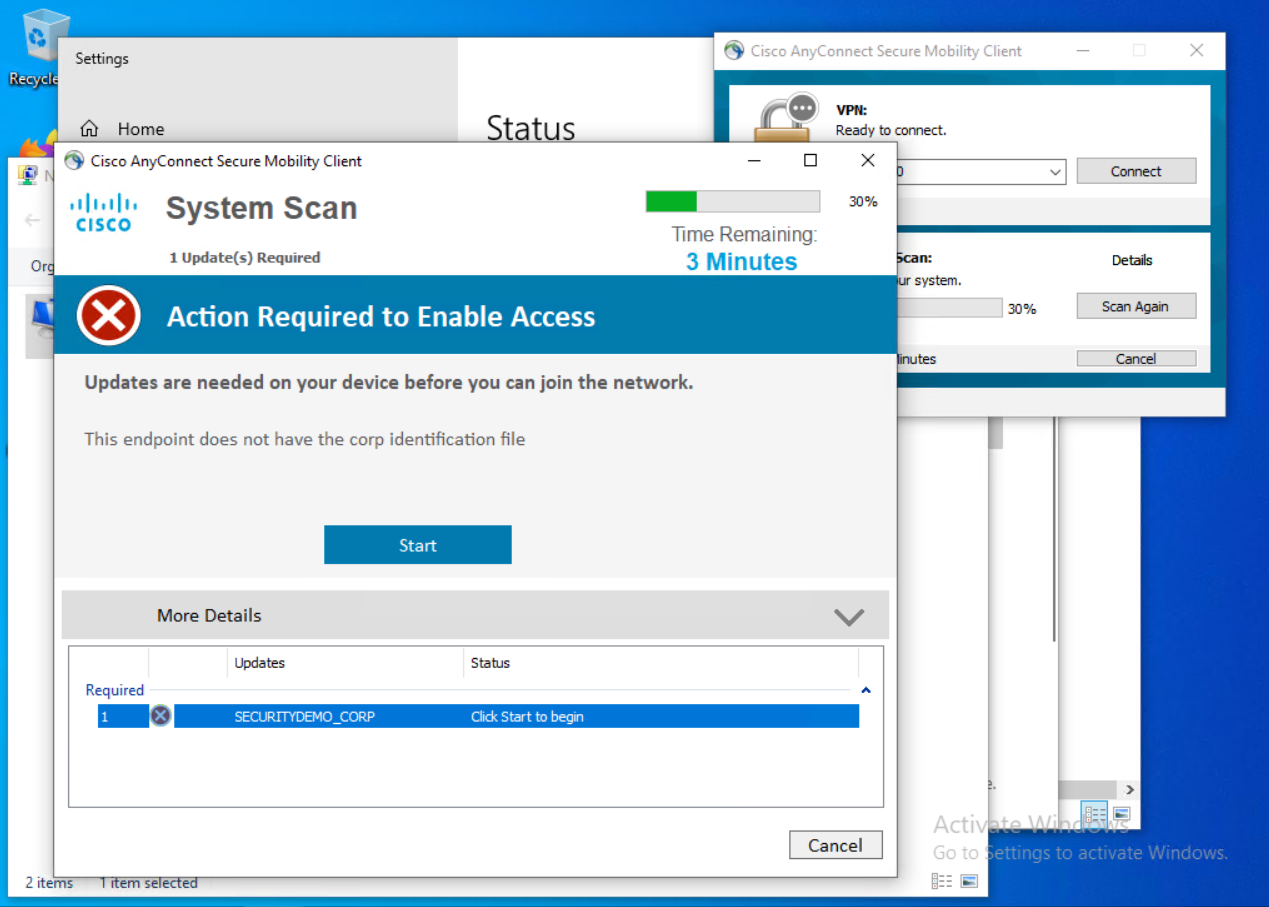
The employee will connect to the network and have a scan run. This example will show what happens when that employee computer fails the posture.
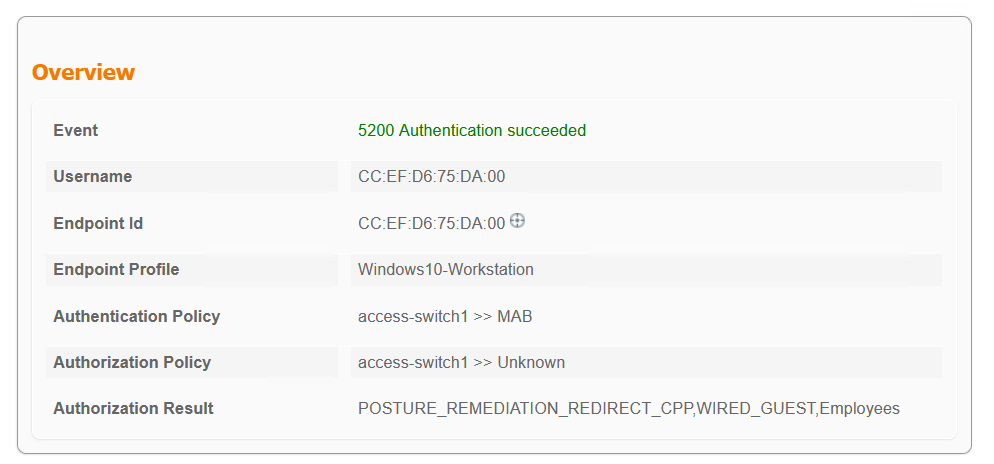
Unknown Compliance Status
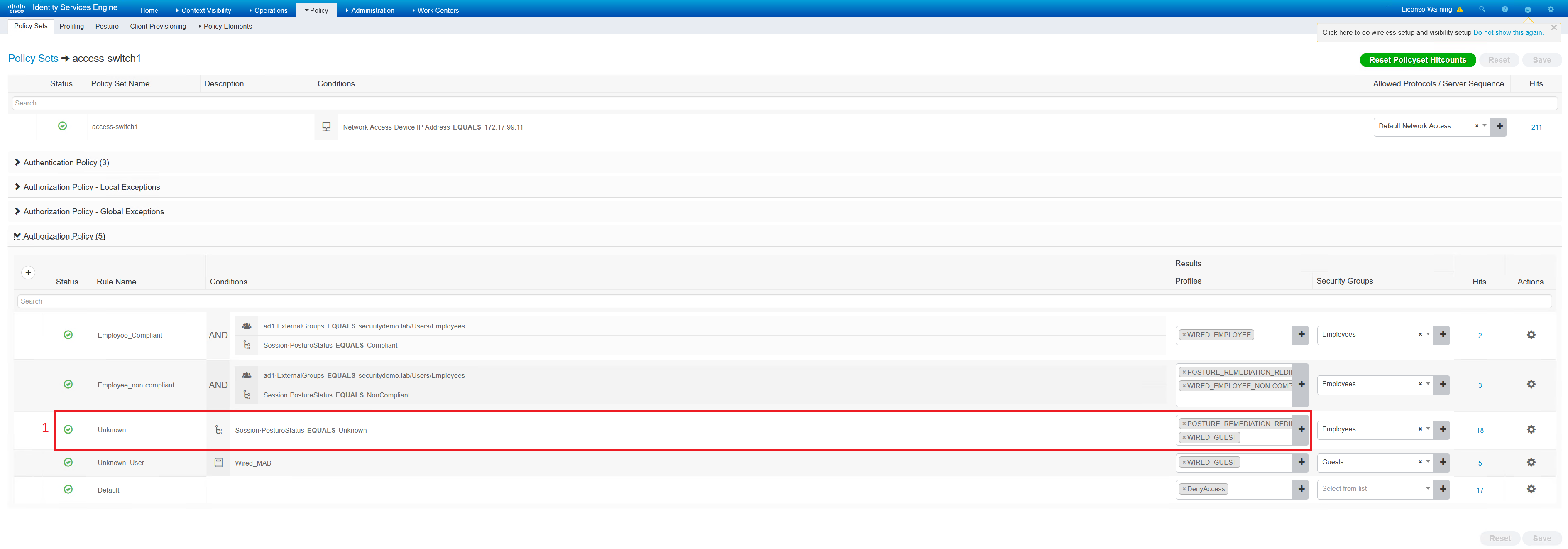
The client is first unknown, they will receive a posture redirect ACL and wired guest ACL. The switchport is configured with the VLAN 70 in network 172.17.70.0/24. The client has a 4 minute grace period to fix their posture status before they are moved to non-compliant posture status.
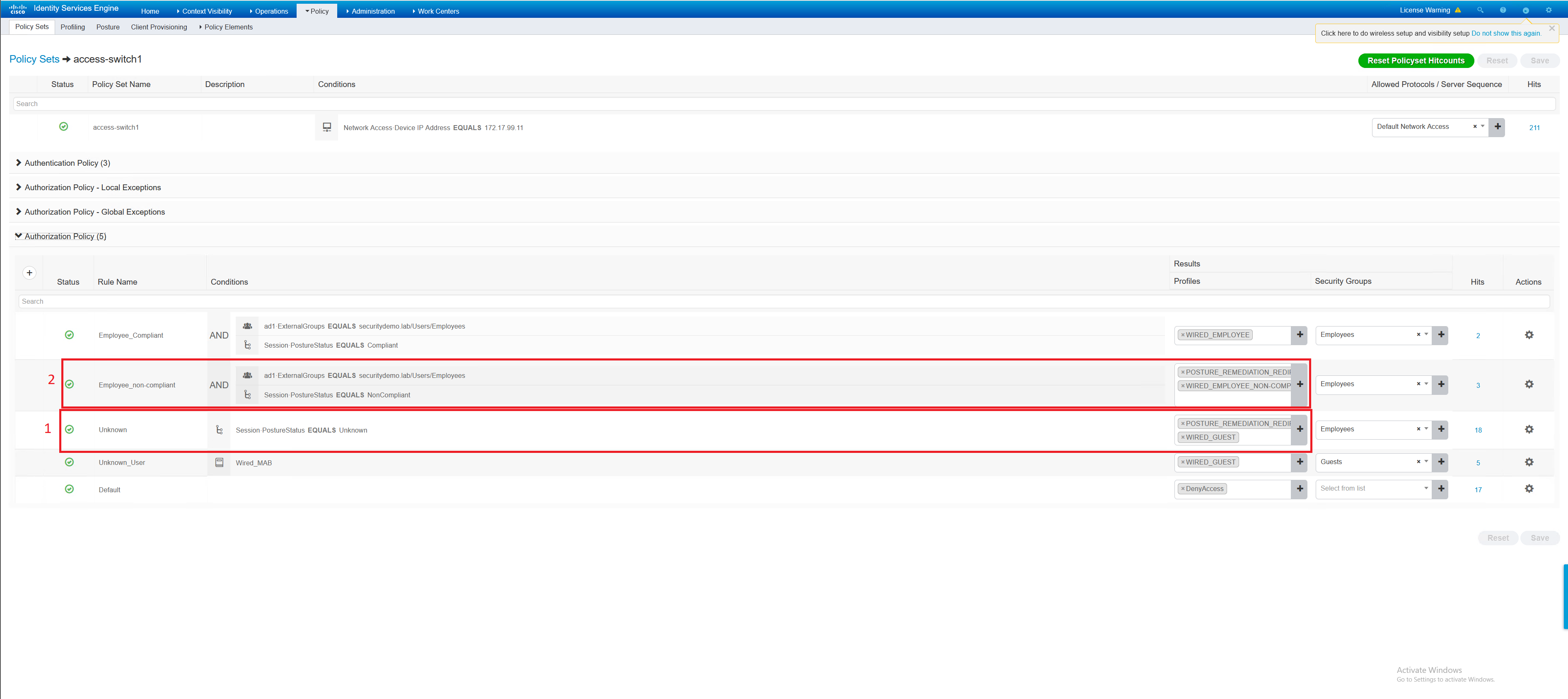
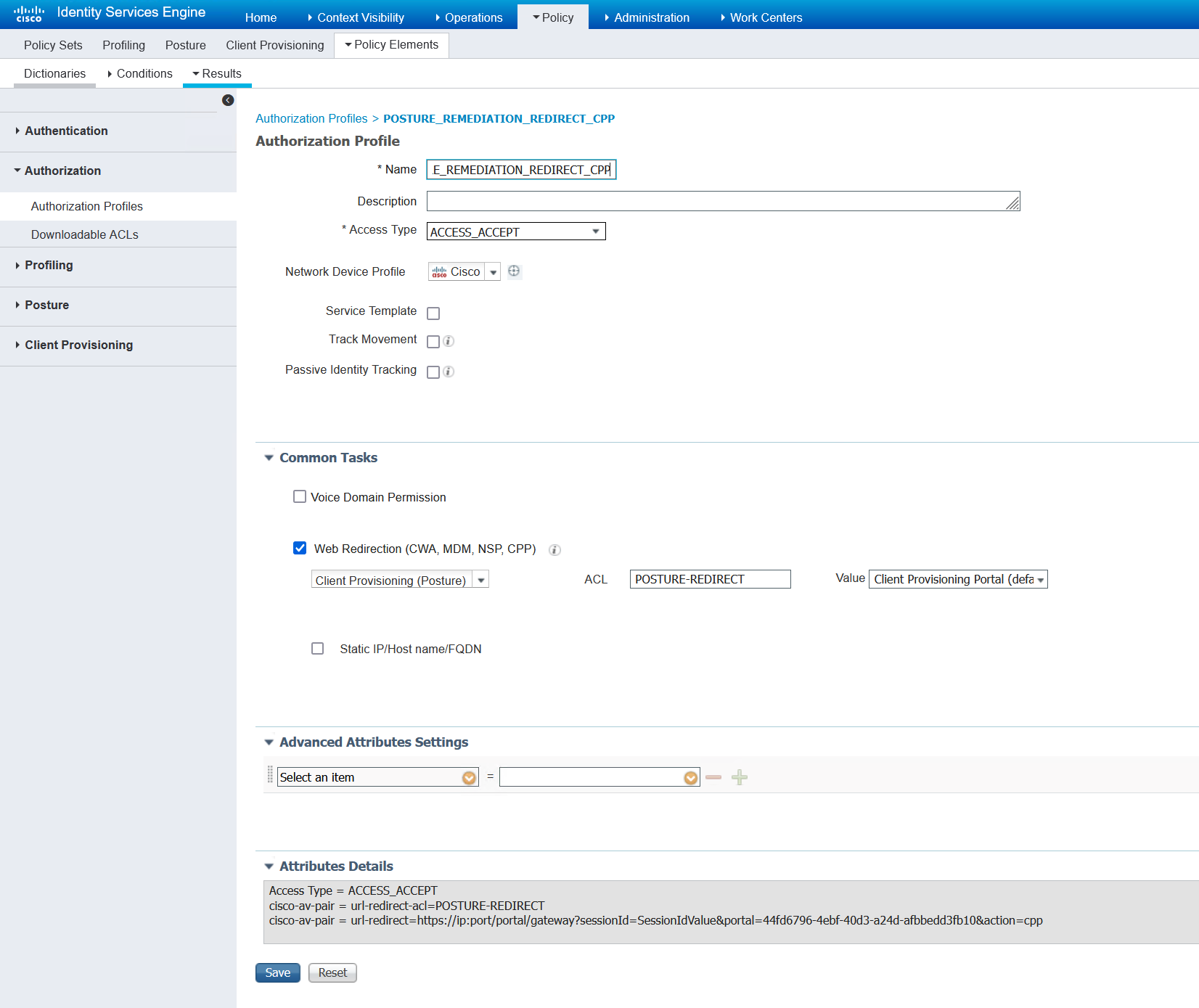
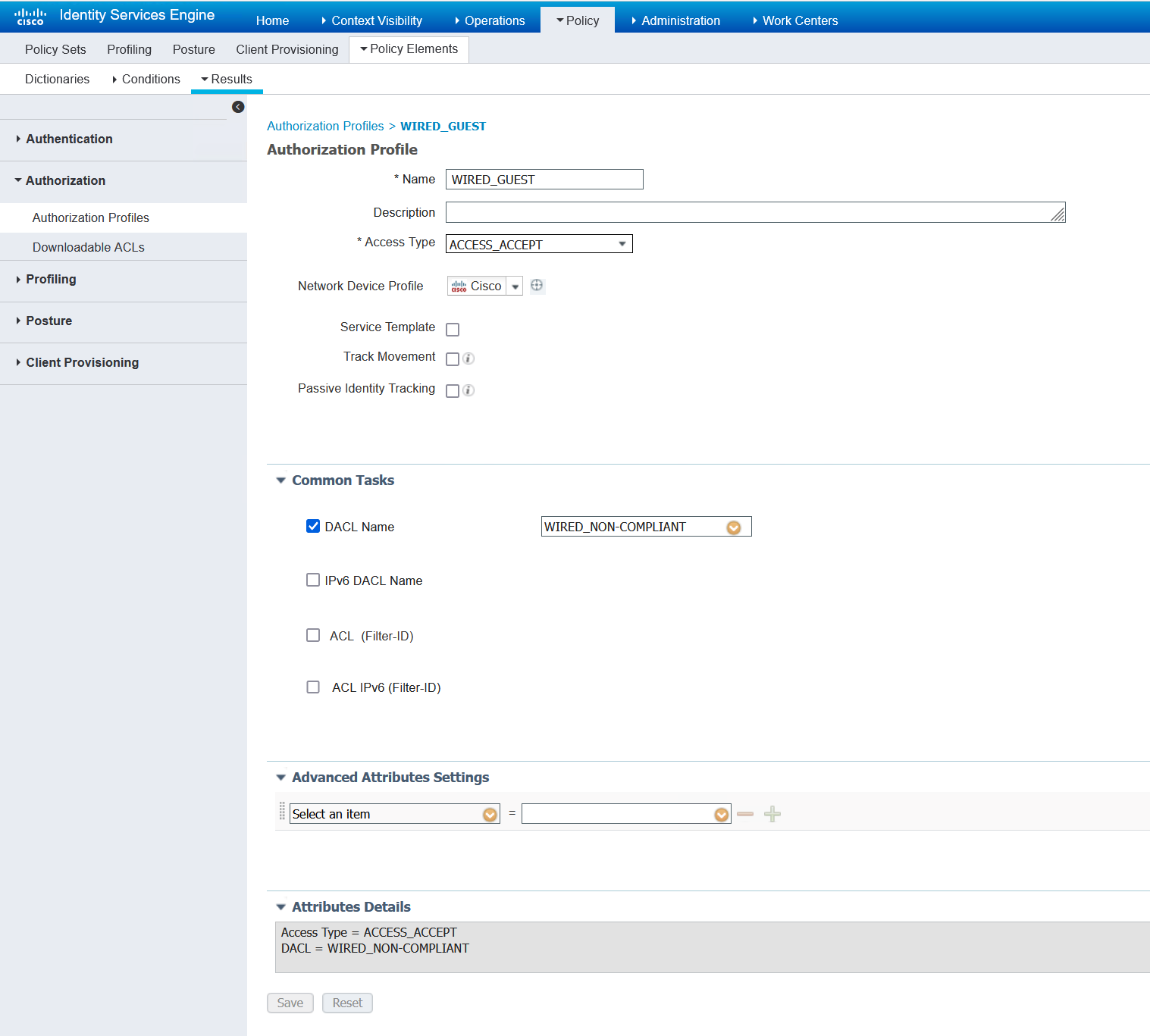
Switch posture redirect ACL referenced by above authorisation profile
|
0 1 2 3 4 5 6 7 8 |
ip access-list extended POSTURE-REDIRECT deny udp any any eq domain deny tcp any any eq domain deny udp any eq bootpc any eq bootps deny tcp any host 172.17.5.101 eq 8443 deny tcp any host 172.17.5.101 eq 8905 deny udp any host 172.17.5.101 eq 8905 |
On the computer, switch and ISE the current unknown or posture remediation looks like…
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 |
access-switch1#sh access-session int gi0/1 details Interface: GigabitEthernet0/1 MAC Address: 0cef.d6ae.ce00 IPv6 Address: Unknown IPv4 Address: 172.17.70.2 User-Name: SECURITYDEMO\Employee1 Status: Authorized Domain: DATA Oper host mode: multi-auth Oper control dir: both Session timeout: N/A Restart timeout: N/A Periodic Acct timeout: 900s (local), Remaining: 875s Session Uptime: 24s Common Session ID: AC11630B0000003B1CCE1C4A Acct Session ID: 0x00000037 Handle: 0xD1000020 Current Policy: DOT1X-DEFAULT Server Policies: URL Redirect: https://ise1.securitydemo.lab:8443/portal/gateway?sessionId=AC11630B0000003B1CCE1C4A&portal=44fd6796-4ebf-40d3-a24d-afbbedd3fb10&action=cpp&token=beb53bc1024e123661eb8c5b8412ebe8 URL Redirect ACL: POSTURE-REDIRECT ACS ACL: xACSACLx-IP-WIRED_NON-COMPLIANT-6391e0db SGT Value: 4 Security Policy: None Security Status: Link Unsecure Method status list: Method State dot1x Authc Success mab Stopped |
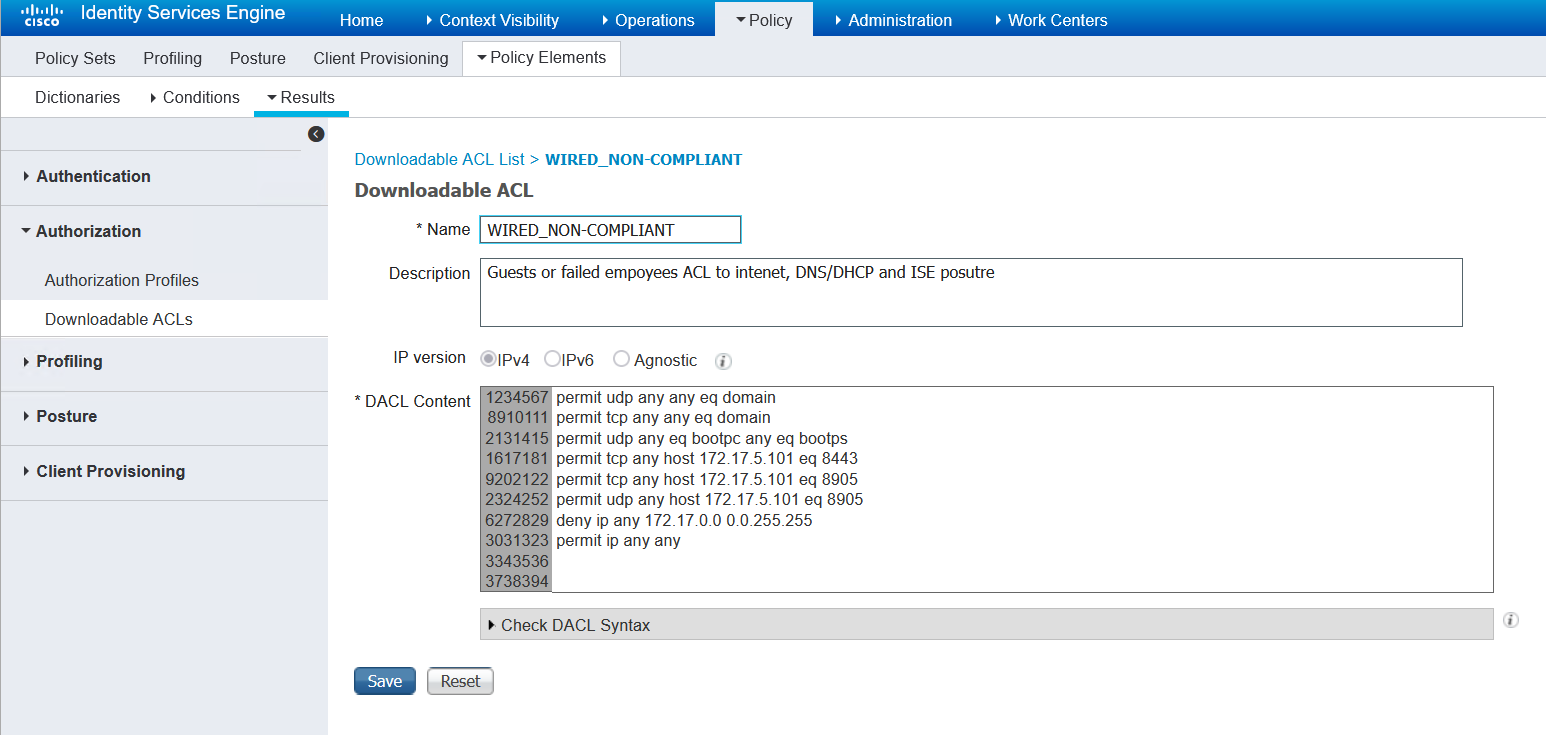
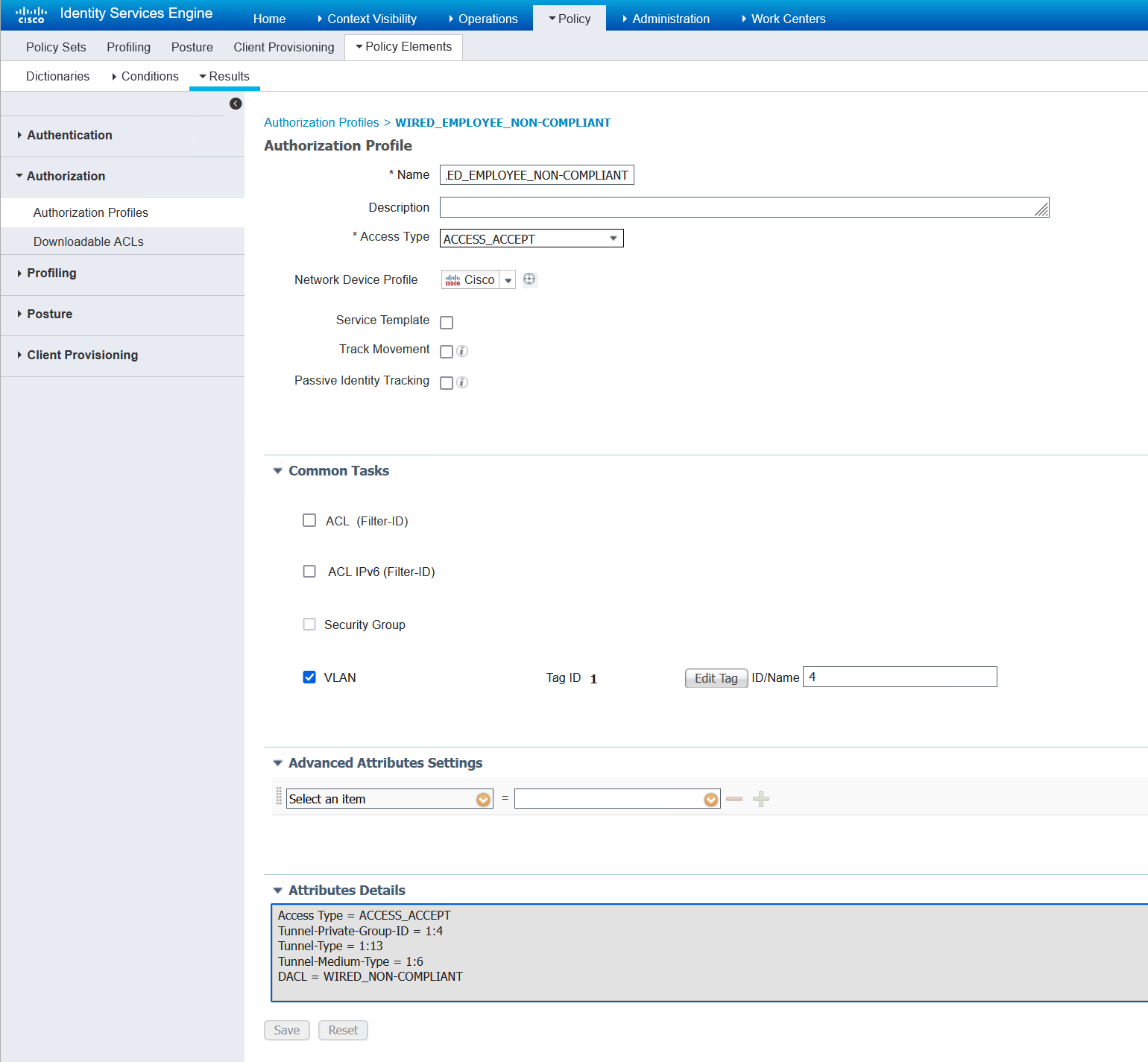
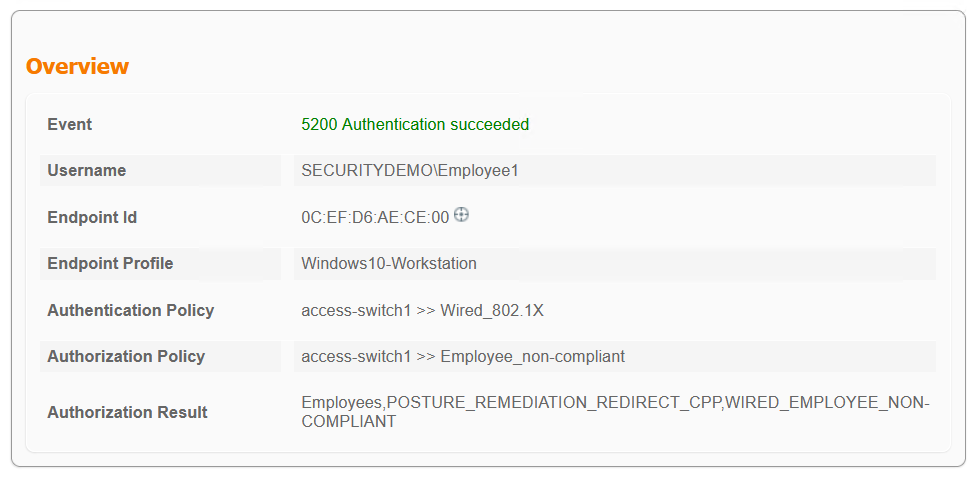
Non-compliant Compliance Status
If the client does not remediate their posture status, so it is successful in the 4 minute time, then they will be placed into VLAN 4 as they are an employee and be give the same access as a guest. So essentially, nothing changes for them access wise. Only the VLAN does.


Switch posture redirect ACL referenced by above authorisation profile
|
0 1 2 3 4 5 6 7 8 |
ip access-list extended POSTURE-REDIRECT deny udp any any eq domain deny tcp any any eq domain deny udp any eq bootpc any eq bootps deny tcp any host 172.17.5.101 eq 8443 deny tcp any host 172.17.5.101 eq 8905 deny udp any host 172.17.5.101 eq 8905 |

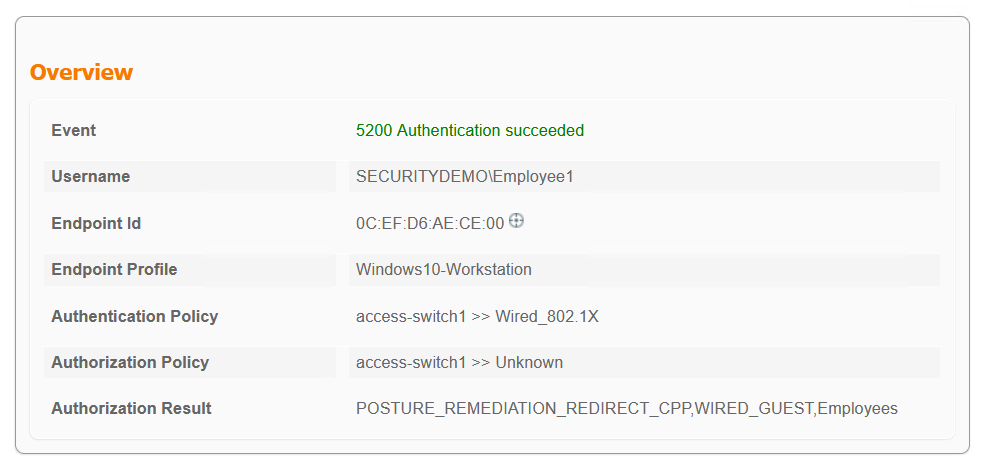
On the computer, switch and ISE the current unknown or posture remediation looks like…
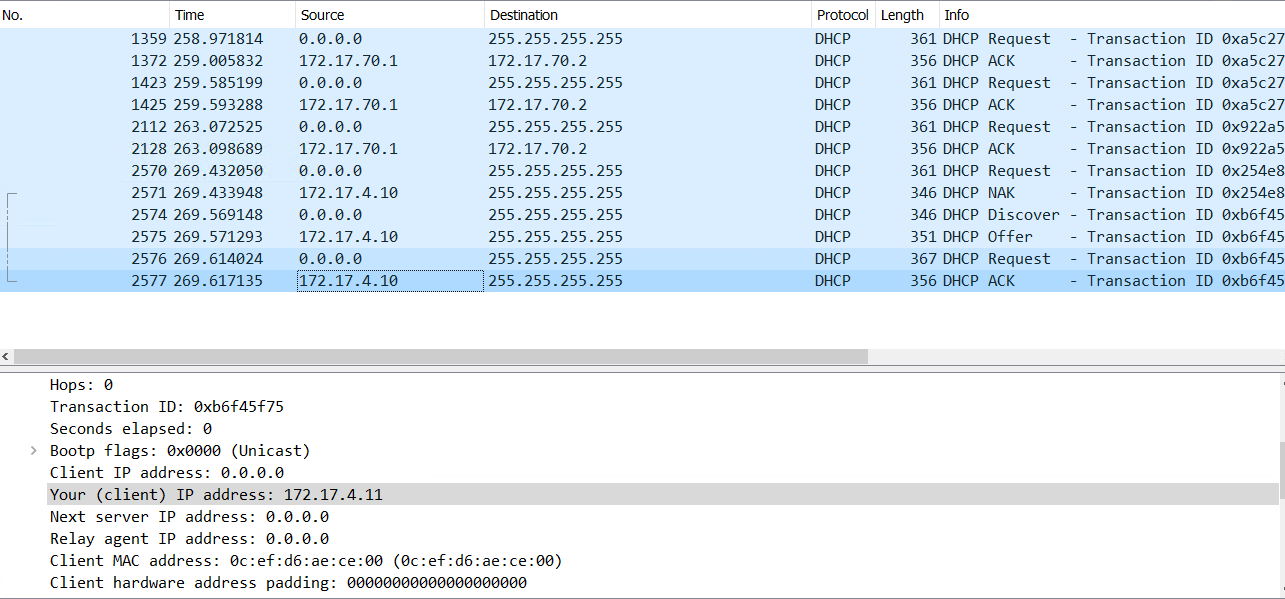
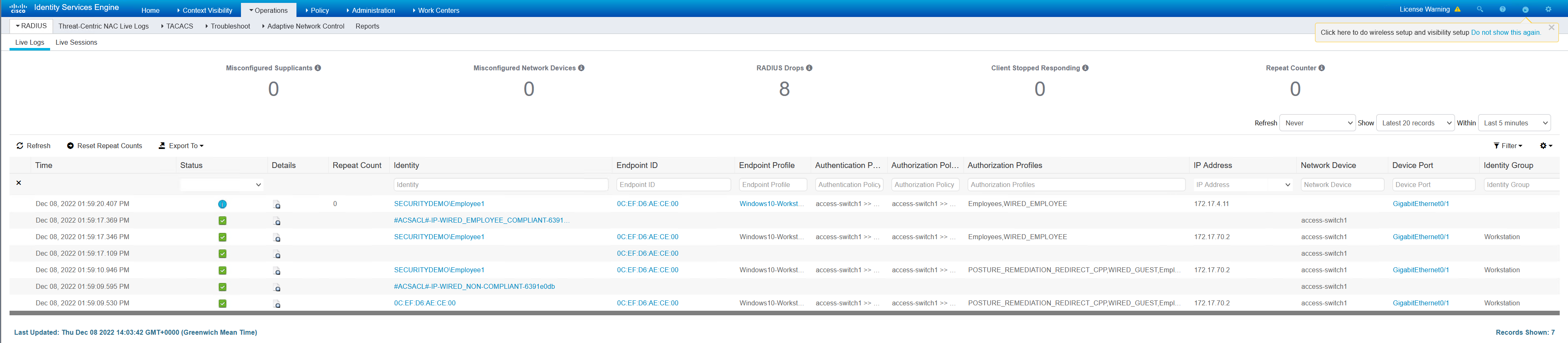
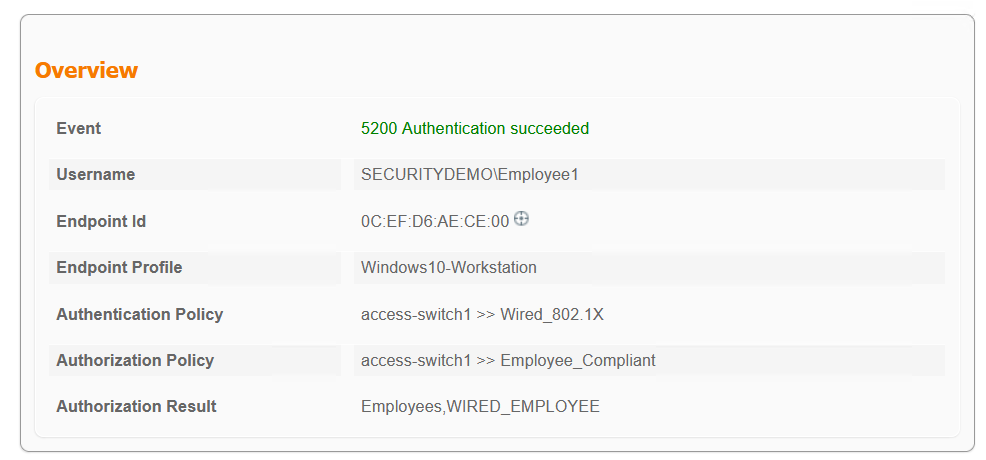
Note how the IP address has changed from 172.17.70.x to 172.17.4.x. This is the result of ISE changing the VLAN. The client has requested a new IP from the DHCP server, which is permitted by the ACLs that it is given.
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
access-switch1#sh access-session int gi0/1 details Interface: GigabitEthernet0/1 MAC Address: 0cef.d6ae.ce00 IPv6 Address: Unknown IPv4 Address: 172.17.4.11 User-Name: SECURITYDEMO\Employee1 Status: Authorized Domain: DATA Oper host mode: multi-auth Oper control dir: both Session timeout: N/A Restart timeout: N/A Periodic Acct timeout: 900s (local), Remaining: 607s Session Uptime: 46s Common Session ID: AC11630B0000003B1CCE1C4A Acct Session ID: 0x00000037 Handle: 0xD1000020 Current Policy: DOT1X-DEFAULT Server Policies: URL Redirect: https://ise1.securitydemo.lab:8443/portal/gateway?sessionId=AC11630B0000003B1CCE1C4A&portal=44fd6796-4ebf-40d3-a24d-afbbedd3fb10&action=cpp&token=2383cc7ba3a8dc714022a2da2521084e URL Redirect ACL: POSTURE-REDIRECT ACS ACL: xACSACLx-IP-WIRED_NON-COMPLIANT-6391e0db SGT Value: 4 Security Policy: None Security Status: Link Unsecure Vlan Group: Vlan: 4 Method status list: Method State dot1x Authc Success mab Stopped |
|
0 1 2 3 4 5 6 7 8 9 10 11 |
access-switch1#sh access-lists xACSACLx-IP-WIRED_NON-COMPLIANT-6391e0db Extended IP access list xACSACLx-IP-WIRED_NON-COMPLIANT-6391e0db (per-user) 1 permit udp any any eq domain 2 permit tcp any any eq domain 3 permit udp any eq bootpc any eq bootps 4 permit tcp any host 172.17.5.101 eq 8443 5 permit tcp any host 172.17.5.101 eq 8905 6 permit udp any host 172.17.5.101 eq 8905 7 deny ip any 172.17.0.0 0.0.255.255 8 permit ip any any |
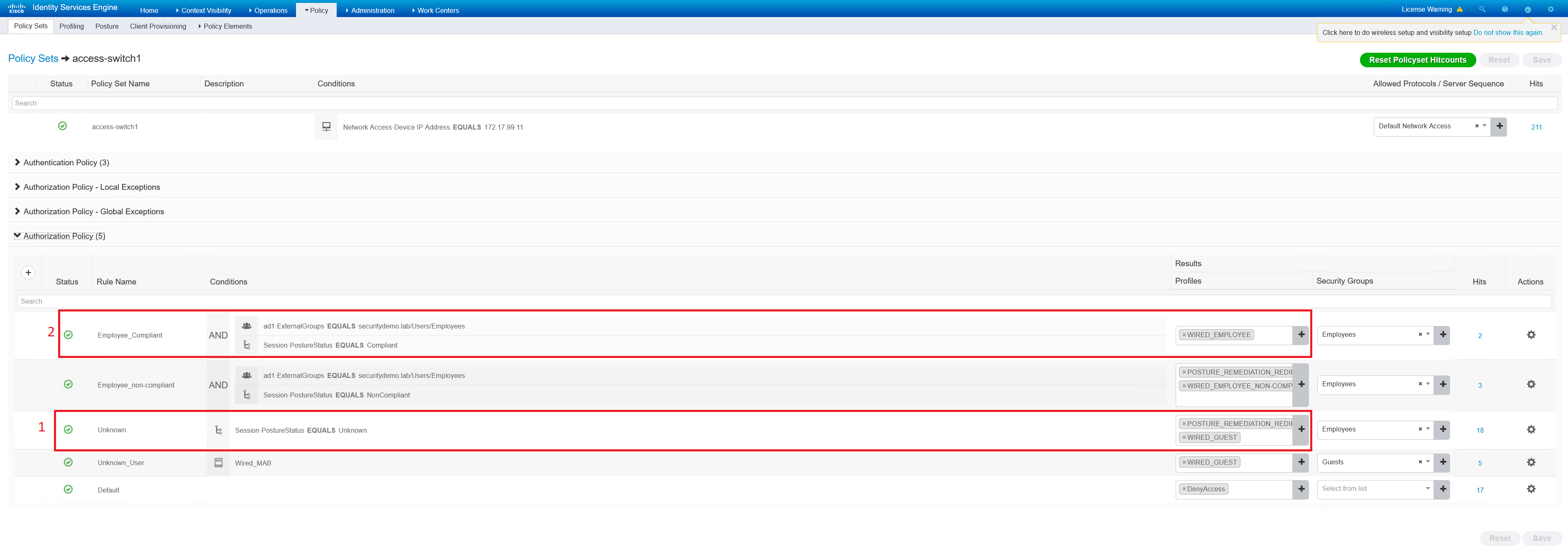
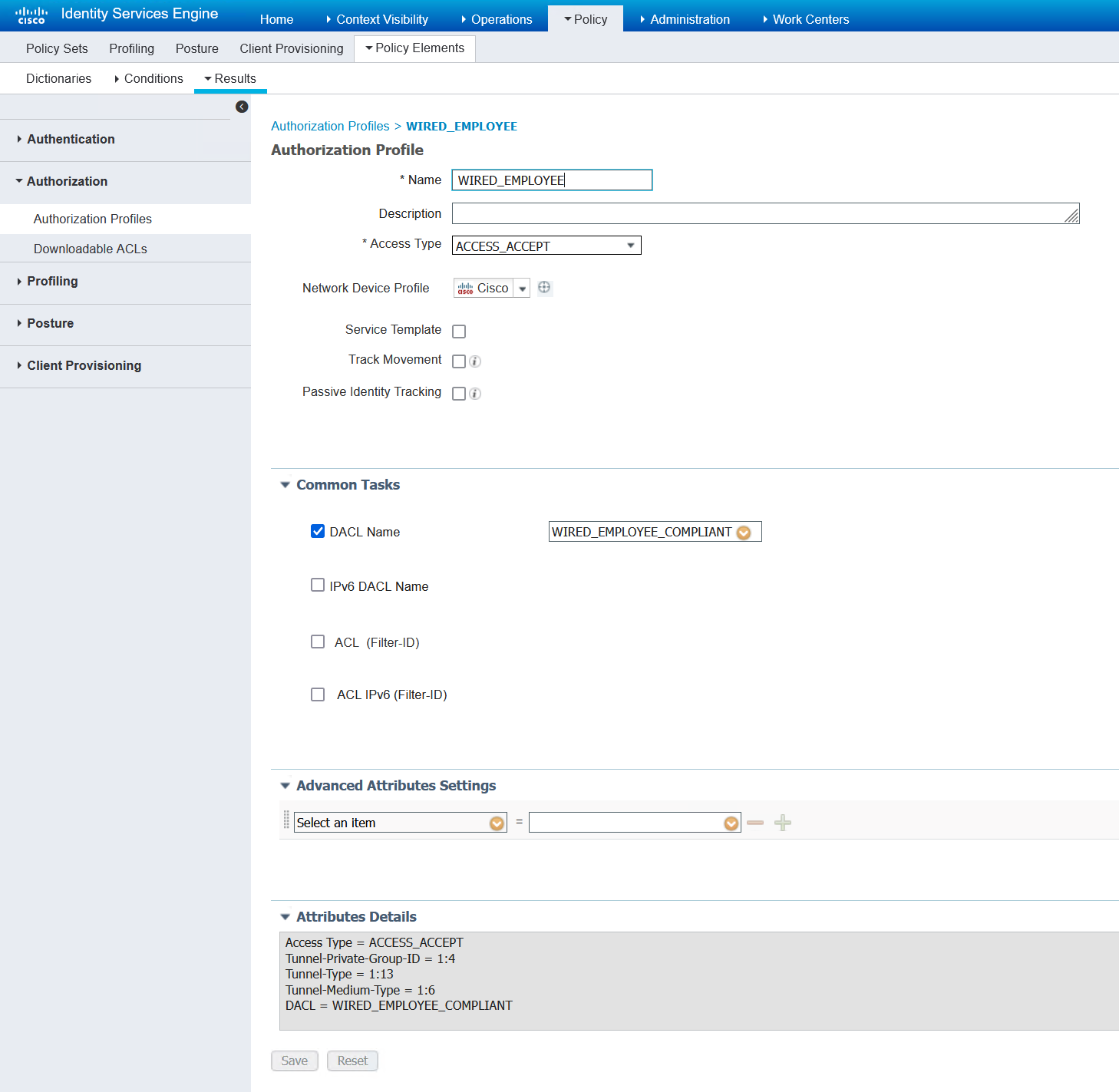
Employee Compliance Posture Success
This process will begin with the same unknown posture status, and then move to compliant very quickly.
The first half will be exactly the same as the unknown posture status above.
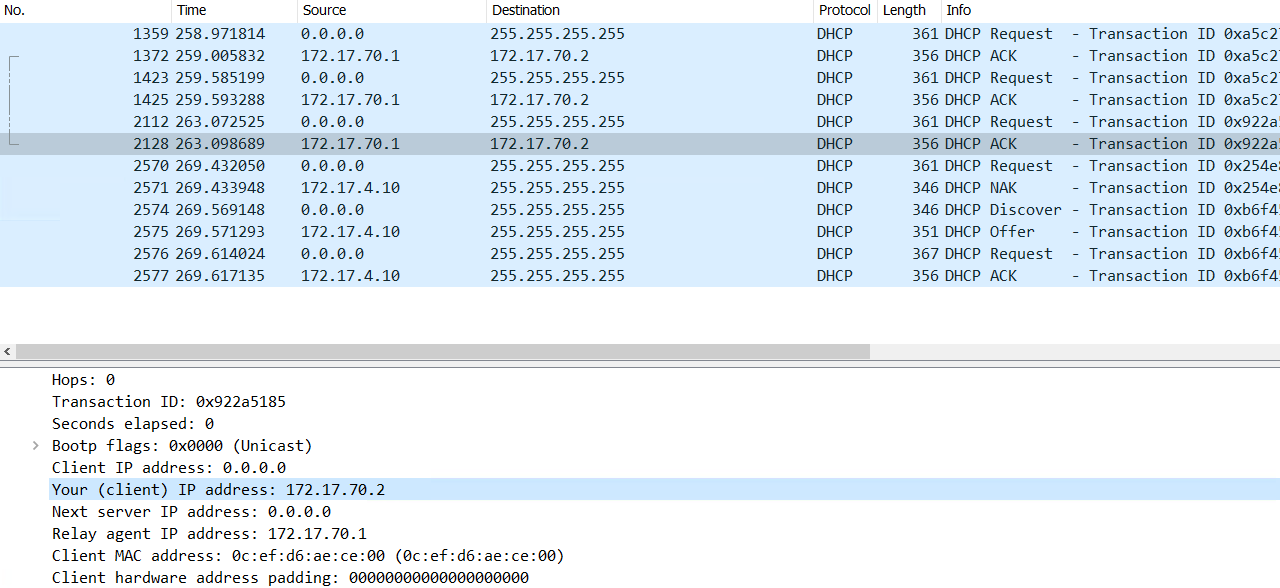
The client will start off in VLAN 70, moving to VLAN 4. There will be two DHCP requests that will be seen in a capture.
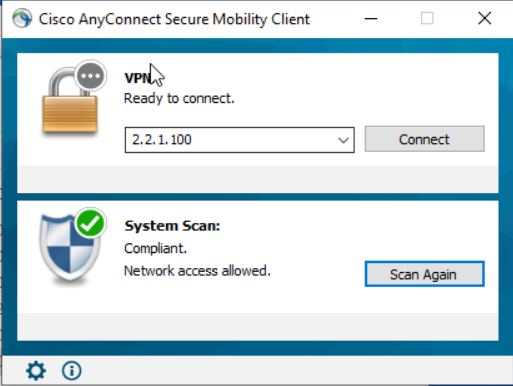
Now to test the client and see that it becomes compliant
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
access-switch1#sh access-session interface gi0/1 det Interface: GigabitEthernet0/1 MAC Address: 0cef.d6ae.ce00 IPv6 Address: Unknown IPv4 Address: 172.17.4.11 User-Name: SECURITYDEMO\Employee1 Status: Authorized Domain: DATA Oper host mode: multi-auth Oper control dir: both Session timeout: N/A Restart timeout: N/A Periodic Acct timeout: 900s (local), Remaining: 720s Session Uptime: 173s Common Session ID: AC11630B0000003E1CF76E16 Acct Session ID: 0x0000003C Handle: 0x0B000022 Current Policy: DOT1X-DEFAULT Server Policies: ACS ACL: xACSACLx-IP-WIRED_EMPLOYEE_COMPLIANT-6391df8d SGT Value: 4 Security Policy: None Security Status: Link Unsecure Vlan Group: Vlan: 4 Method status list: Method State dot1x Authc Success mab Stopped |
|
0 1 2 3 4 |
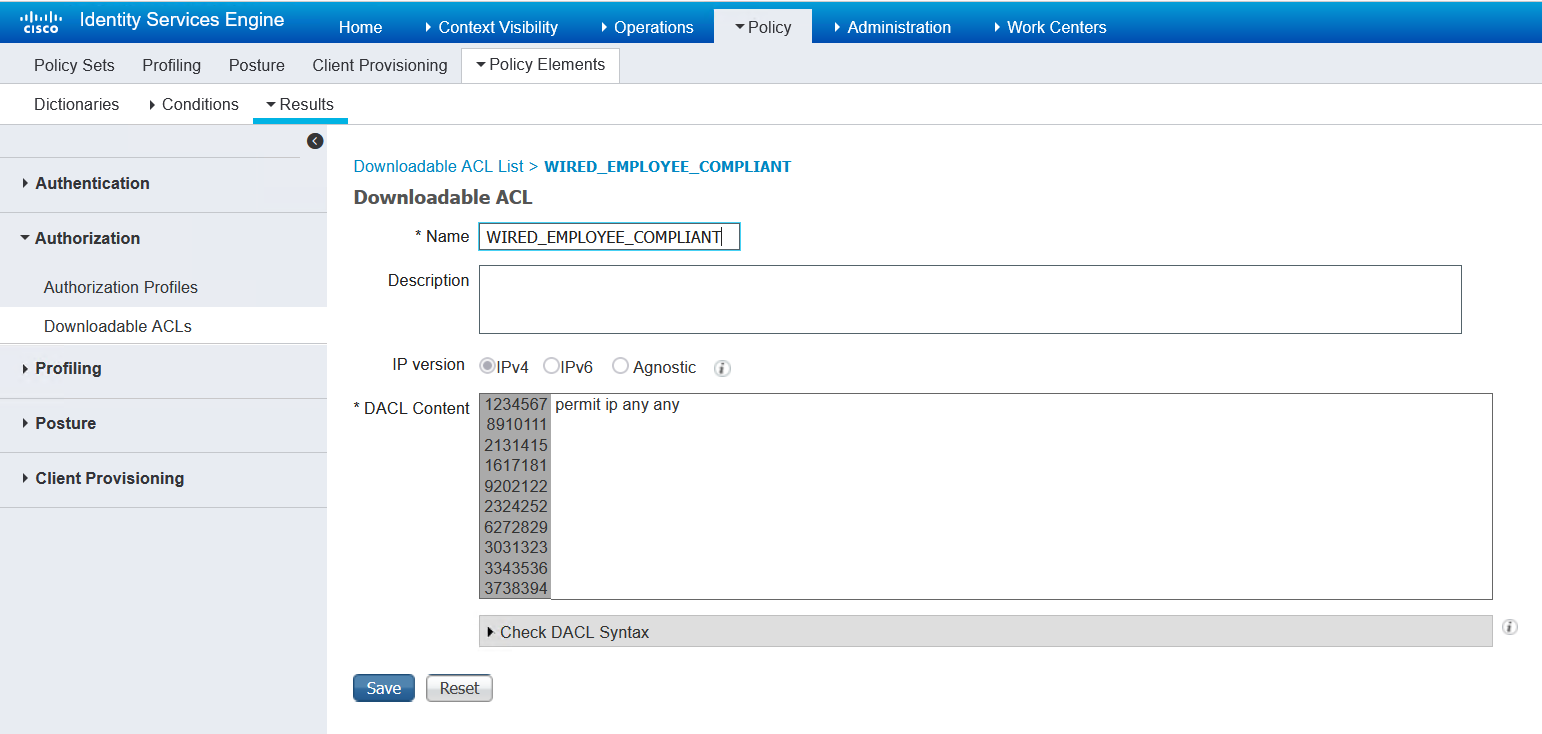
access-switch1#$ sh ip access-lists xACSACLx-IP-WIRED_EMPLOYEE_COMPLIANT-6391df8d Extended IP access list xACSACLx-IP-WIRED_EMPLOYEE_COMPLIANT-6391df8d (per-user) 1 permit ip any any |
Guest Compliance Fail
This type of user is expected to fail. The only difference between the guest user and the employees are that the guest user will remain in VLAN 70.
The guests will stay on the first step, never moving to non-compliant status.
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
access-switch1#sh access-session int gi0/1 details Interface: GigabitEthernet0/1 MAC Address: ccef.d675.da00 IPv6 Address: Unknown IPv4 Address: 172.17.70.3 User-Name: CC-EF-D6-75-DA-00 Status: Authorized Domain: DATA Oper host mode: multi-auth Oper control dir: both Session timeout: N/A Restart timeout: N/A Periodic Acct timeout: 900s (local), Remaining: 467s Session Uptime: 433s Common Session ID: AC11630B000000401D044EEB Acct Session ID: 0x0000003F Handle: 0x89000024 Current Policy: DOT1X-DEFAULT Server Policies: URL Redirect: https://ise1.securitydemo.lab:8443/portal/gateway?sessionId=AC11630B000000401D044EEB&portal=44fd6796-4ebf-40d3-a24d-afbbedd3fb10&action=cpp&token=1cbf0481608613ba89ac0ed5022a5818 URL Redirect ACL: POSTURE-REDIRECT ACS ACL: xACSACLx-IP-WIRED_NON-COMPLIANT-6391e0db SGT Value: 4 Method status list: Method State dot1x Stopped mab Authc Success |
|
0 1 2 3 4 5 6 7 8 9 10 11 |
access-switch1#sh ip access-lists xACSACLx-IP-WIRED_NON-COMPLIANT-6391e0db Extended IP access list xACSACLx-IP-WIRED_NON-COMPLIANT-6391e0db (per-user) 1 permit udp any any eq domain 2 permit tcp any any eq domain 3 permit udp any eq bootpc any eq bootps 4 permit tcp any host 172.17.5.101 eq 8443 5 permit tcp any host 172.17.5.101 eq 8905 6 permit udp any host 172.17.5.101 eq 8905 7 deny ip any 172.17.0.0 0.0.255.255 8 permit ip any any |