Now that the API has been configured, it can be tested. In this post, I will show a few base GET requests that can be made to ISE in Postman.
There is a lot of documentation built into ISE to view which gives examples on the types of calls and examples of calls and returned output.
https://172.17.5.101:9060/ers/sdk#_
I am going to use Postman, as my ISE server is not using an SSL certificate signed by a public CA, any certificate checking that Postman does will fail. Therefore, I have disabled certificate checking in the settings.
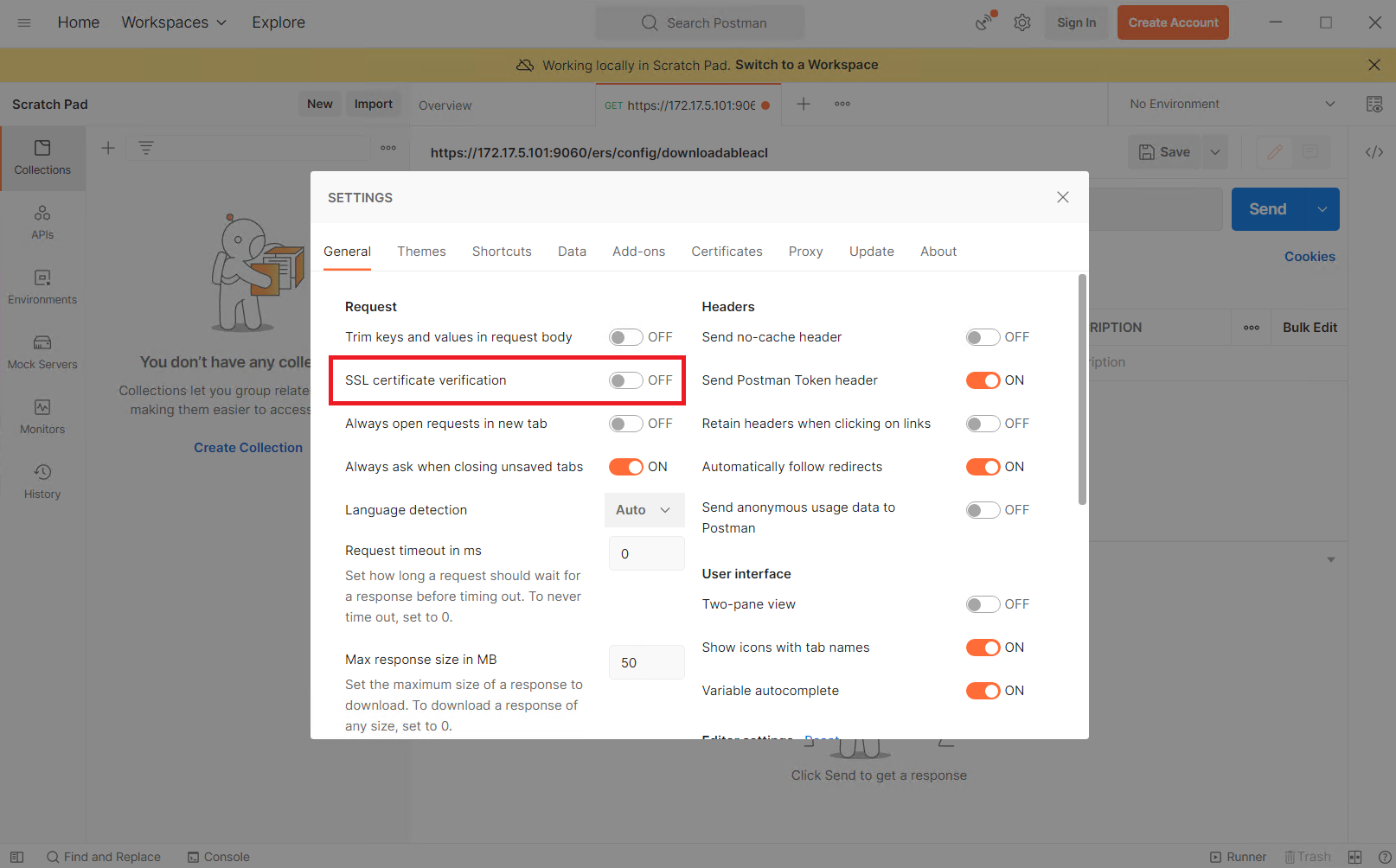
The GET request I will run will be to gather all the downloadable ACLs that are present.
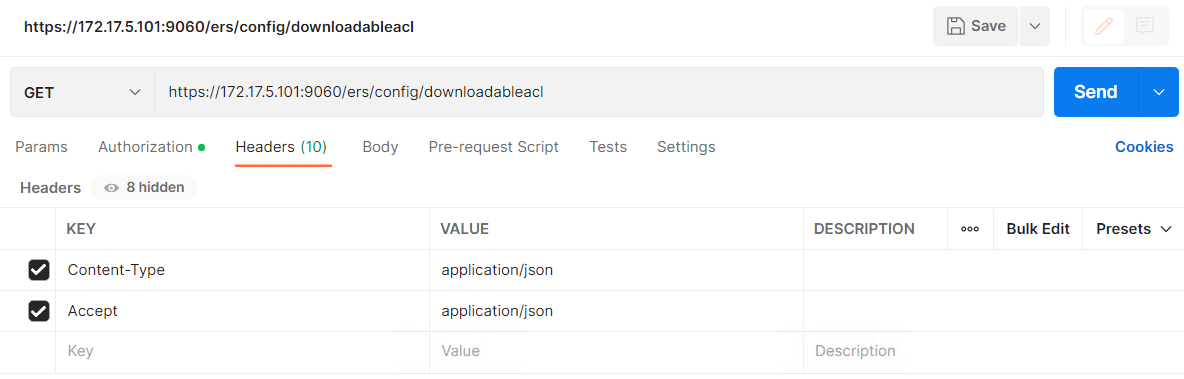
Postman needs to be configured before the request can be sent.
– First, there needs the authorisation header, which can be the basic username/password.
– Second, there needs to be two additional headers. HTTP ‘Content-Type’ Header and HTTP ‘Accept’ Header.
The API reference documentation that is on ISE has the fields there so it makes quite simple.
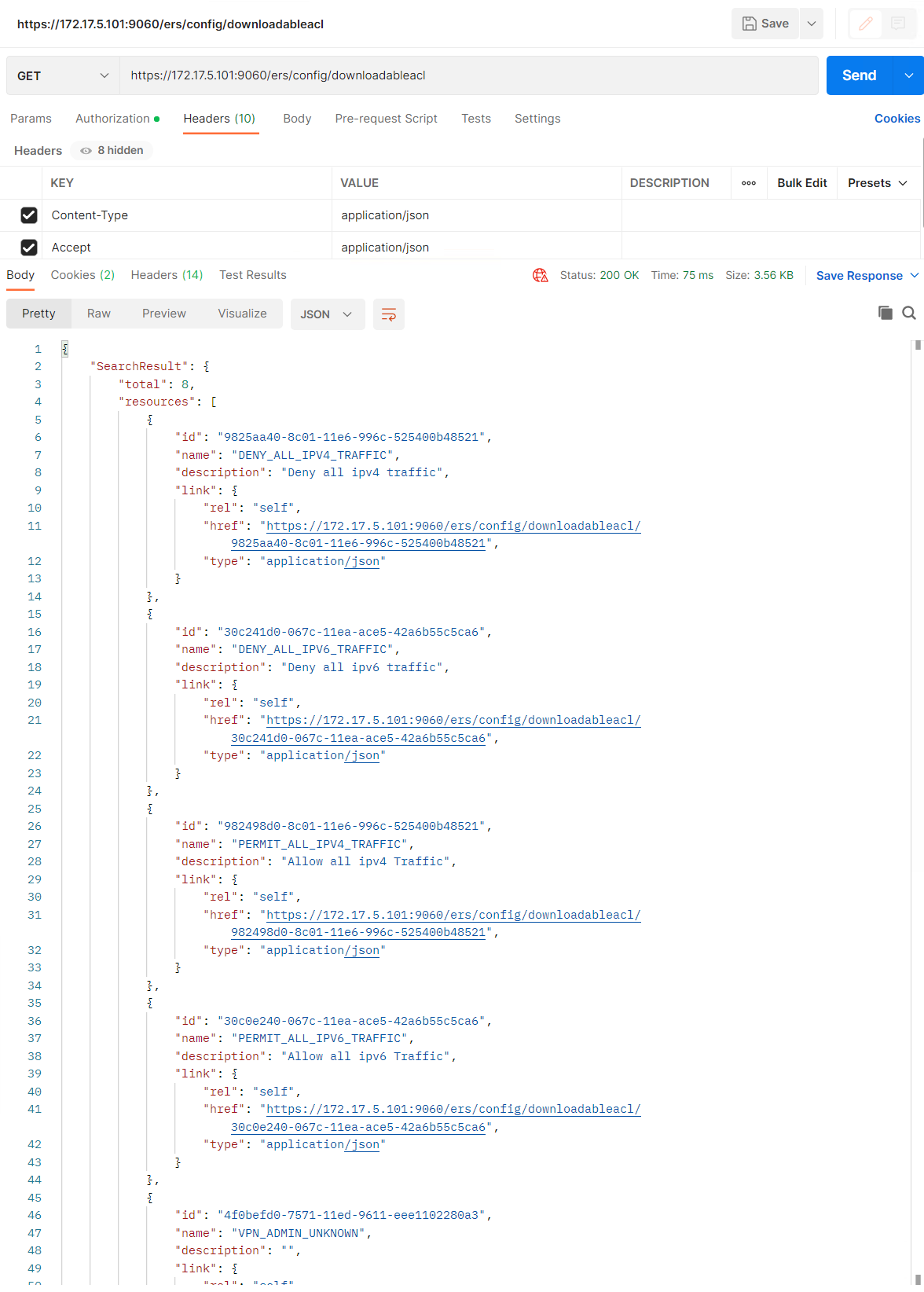
All of the dACLs can be seen, there is no ACL configuration lines for that the id must be used
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 |
{ "SearchResult": { "total": 8, "resources": [ { "id": "9825aa40-8c01-11e6-996c-525400b48521", "name": "DENY_ALL_IPV4_TRAFFIC", "description": "Deny all ipv4 traffic", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/9825aa40-8c01-11e6-996c-525400b48521", "type": "application/json" } }, { "id": "30c241d0-067c-11ea-ace5-42a6b55c5ca6", "name": "DENY_ALL_IPV6_TRAFFIC", "description": "Deny all ipv6 traffic", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/30c241d0-067c-11ea-ace5-42a6b55c5ca6", "type": "application/json" } }, { "id": "982498d0-8c01-11e6-996c-525400b48521", "name": "PERMIT_ALL_IPV4_TRAFFIC", "description": "Allow all ipv4 Traffic", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/982498d0-8c01-11e6-996c-525400b48521", "type": "application/json" } }, { "id": "30c0e240-067c-11ea-ace5-42a6b55c5ca6", "name": "PERMIT_ALL_IPV6_TRAFFIC", "description": "Allow all ipv6 Traffic", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/30c0e240-067c-11ea-ace5-42a6b55c5ca6", "type": "application/json" } }, { "id": "4f0befd0-7571-11ed-9611-eee1102280a3", "name": "VPN_ADMIN_UNKNOWN", "description": "", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/4f0befd0-7571-11ed-9611-eee1102280a3", "type": "application/json" } }, { "id": "68205db0-725d-11ed-9611-eee1102280a3", "name": "WIRED_COMPUTER", "description": "", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/68205db0-725d-11ed-9611-eee1102280a3", "type": "application/json" } }, { "id": "827e1760-725d-11ed-9611-eee1102280a3", "name": "WIRED_EMPLOYEE_COMPLIANT", "description": "", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/827e1760-725d-11ed-9611-eee1102280a3", "type": "application/json" } }, { "id": "cefc1f70-76f8-11ed-9611-eee1102280a3", "name": "WIRED_NON-COMPLIANT", "description": "Guests or failed empoyees ACL to intenet, DNS/DHCP and ISE posutre", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/cefc1f70-76f8-11ed-9611-eee1102280a3", "type": "application/json" } } ] } } |
To see exactly what ACL configuration is in the dACL the id is used.
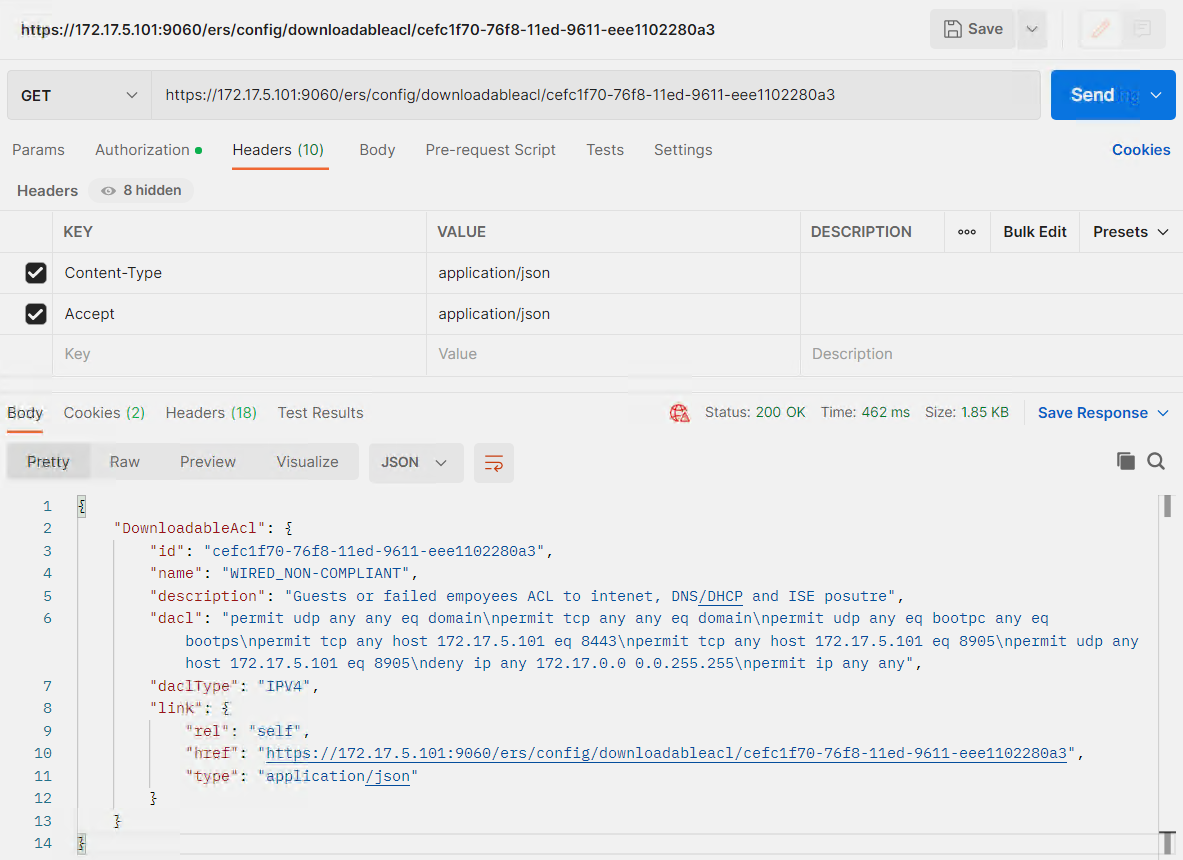
Running this GET request in Postman gives the following output. Note how the description and config is included.
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
{ "DownloadableAcl": { "id": "cefc1f70-76f8-11ed-9611-eee1102280a3", "name": "WIRED_NON-COMPLIANT", "description": "Guests or failed empoyees ACL to intenet, DNS/DHCP and ISE posutre", "dacl": "permit udp any any eq domain\npermit tcp any any eq domain\npermit udp any eq bootpc any eq bootps\npermit tcp any host 172.17.5.101 eq 8443\npermit tcp any host 172.17.5.101 eq 8905\npermit udp any host 172.17.5.101 eq 8905\ndeny ip any 172.17.0.0 0.0.255.255\npermit ip any any", "daclType": "IPV4", "link": { "rel": "self", "href": "https://172.17.5.101:9060/ers/config/downloadableacl/cefc1f70-76f8-11ed-9611-eee1102280a3", "type": "application/json" } } } |
