Creating GitLab Project
I have started this off by creating a new in GitLab. As I have previously setup my SSH key for GitLab I will just clone the repo and I’ll be able to push changes that way.
|
0 1 2 |
git clone git@gitlab.com:ntwklab1/asaterraform.git |
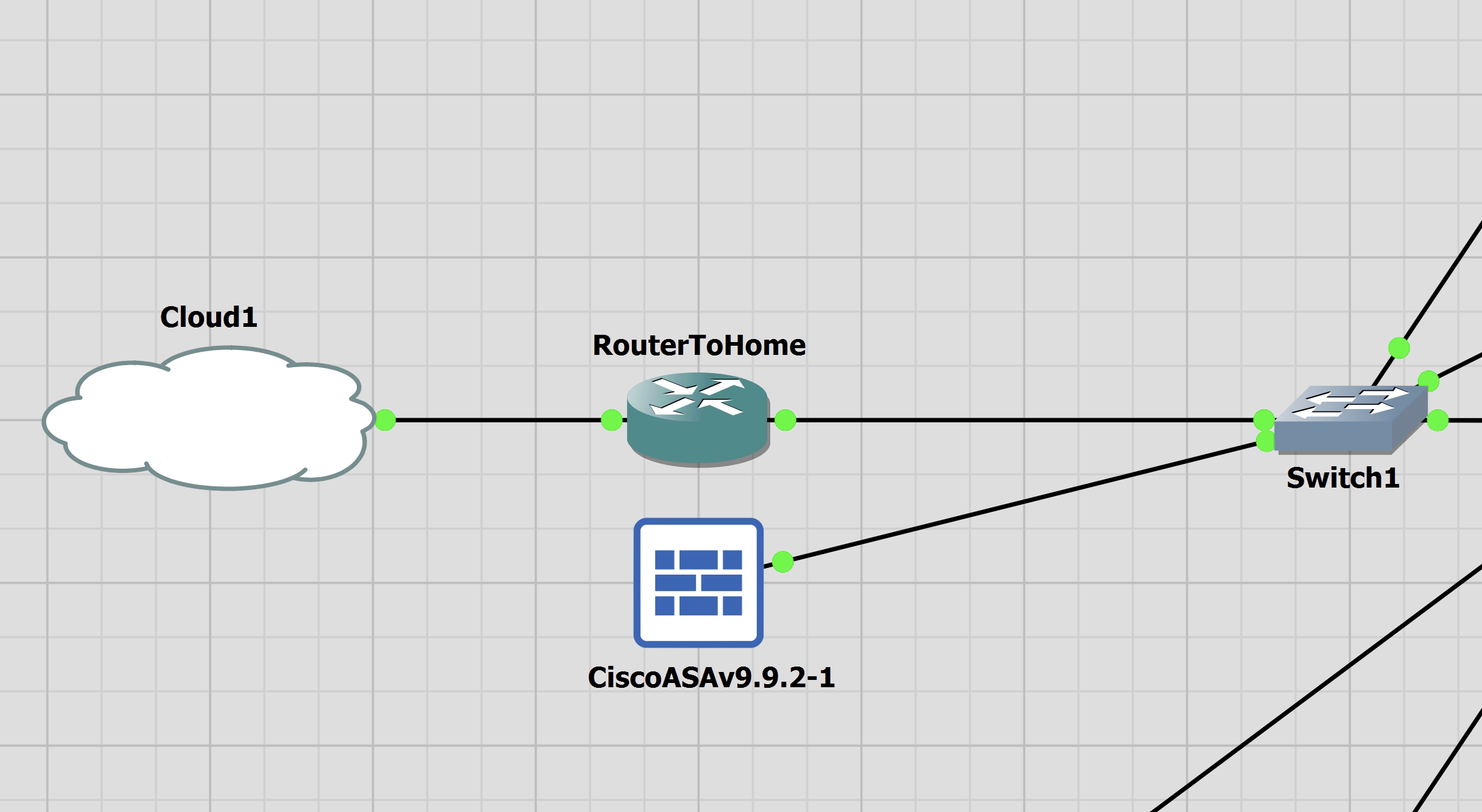
My lab is up and running GNS3, I just ensure that I can ping and SSH to the ASA from my Ubuntu VM.
|
0 1 2 3 |
ping 172.16.1.250 ssh admin@172.16.1.250 |
I’ll create two files; .gitignore and main.tf and push them upto the new repo. The main.tf file I will be focussing on next.
|
0 1 2 3 4 5 6 7 |
touch .gitignore touch main.tf git add * git commit -am "adding new terraform and ignore files" git push |
Basic Terraform
The Terraform provider I am using can be found here. There has been a change from 1.2 to 1.3. The provider should now be used in the following way.
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
terraform { required_providers { ciscoasa = { source = "CiscoDevNet/ciscoasa" version = "1.3.0" } } } provider "ciscoasa" { api_url = "https://172.16.1.250" username = "admin" password = "Stefan2020" ssl_no_verify = true } |
Create Interface with Terraform
I will start by showing a a basic physial interface creation with Terraform.
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 |
resource "ciscoasa_interface_physical" "gig1_inside" { name = "INSIDE" hardware_id = "GigabitEthernet0/1" interface_desc = "INSIDE_TERRAFORM_CREATED" ip_address { static { ip = "10.101.1.1" net_mask = "255.255.255.0" } } security_level = 100 } |
Now to initialise Terraform and then apply the config.
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
terraform init $ terraform init Initializing the backend... Initializing provider plugins... - Reusing previous version of ciscodevnet/ciscoasa from the dependency lock file - Using previously-installed ciscodevnet/ciscoasa v1.3.0 Terraform has been successfully initialized! You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary. |
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 |
$ terraform apply Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following symbols: + create Terraform will perform the following actions: # ciscoasa_interface_physical.gig1_inside will be created + resource "ciscoasa_interface_physical" "gig1_inside" { + forward_traffic_cx = false + forward_traffic_sfr = false + hardware_id = "GigabitEthernet0/1" + id = (known after apply) + interface_desc = "INSIDE_TERRAFORM_CREATED" + last_updated = (known after apply) + management_only = false + mtu = 1500 + name = "INSIDE" + security_level = 100 + shutdown = true + ip_address { + dhcp = [] + static = [ + { + ip = "10.101.1.1" + net_mask = "255.255.255.0" }, ] } } Plan: 1 to add, 0 to change, 0 to destroy. Do you want to perform these actions? Terraform will perform the actions described above. Only 'yes' will be accepted to approve. Enter a value: yes ciscoasa_interface_physical.gig1_inside: Creating... ciscoasa_interface_physical.gig1_inside: Creation complete after 2s [id=GigabitEthernet0_API_SLASH_1] Apply complete! Resources: 1 added, 0 changed, 0 destroyed. |
Terraform has deployed the new interface to the ASA. By SSHing to the ASA I can see the new interface that has been configured.
|
0 1 2 3 4 5 6 7 8 9 |
ASA1# sh run int gi 0/1 ! interface GigabitEthernet0/1 description INSIDE_TERRAFORM_CREATED shutdown nameif INSIDE security-level 100 ip address 10.101.1.1 255.255.255.0 |
