This post will be an overview of the project progress for Firewall Rule Self-Service portal that I am creating with Go.
The code can be found as release v0.02 in my GitHub
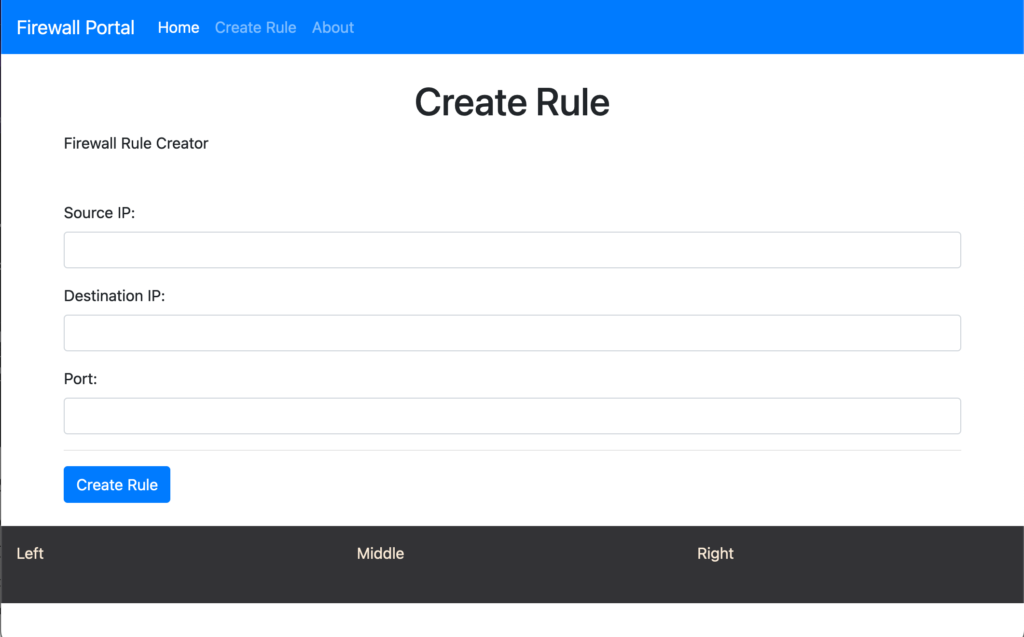
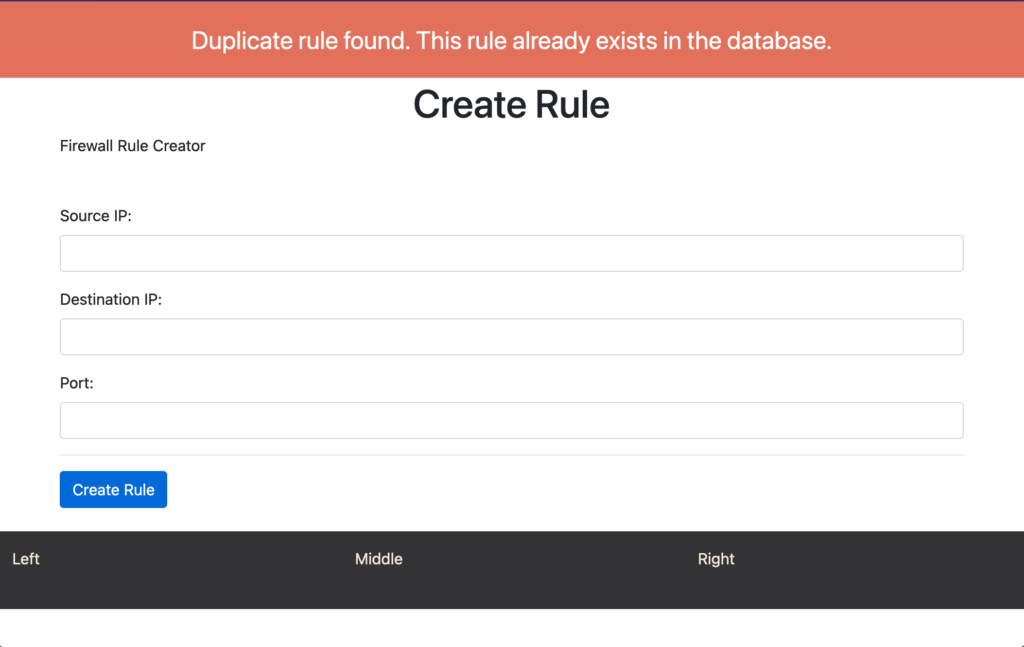
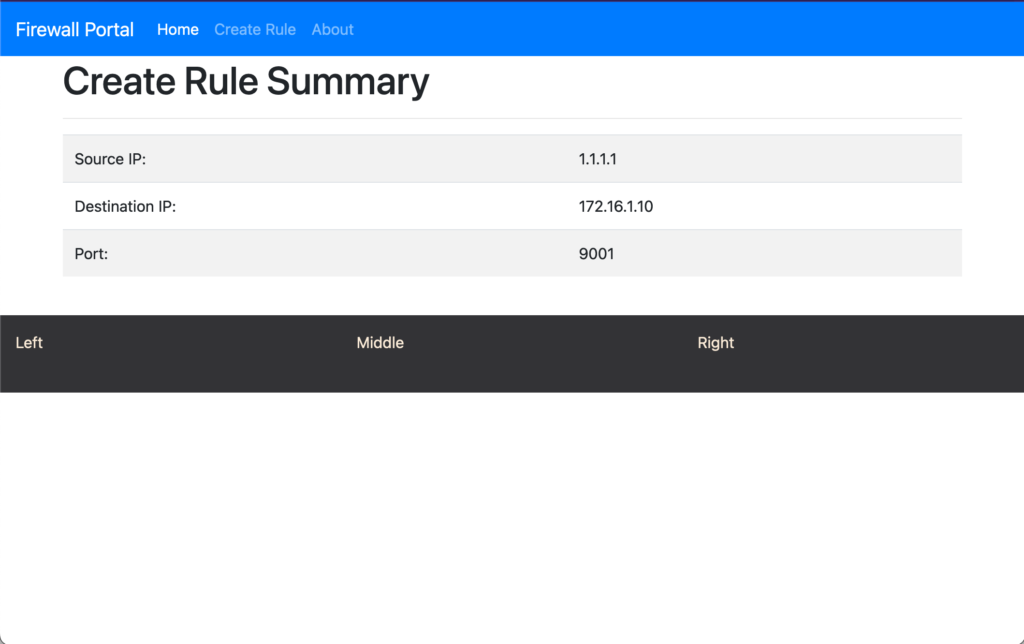
The project is to allow non-technical users to create a firewall rule in Terraform. Currently, the project has a single main page, which is the /create-rule page. This is where the user will provide the rule details required, this will test to see if the database has a duplicate rule, if so an error message is displayed. If the rule is unique, then a summary page is displayed and a Terraform file is appended in the root of the project directory.
|
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
% ./run.sh 2023/11/27 00:06:17 Connecting to the database... 2023/11/27 00:06:17 Connected to the database! Starting application on port :8010 resource "ciscoasa_access_in_rules" "1.1.1.1_172.16.1.10_9001" { interface = "OUTSIDE" rule { source = "1.1.1.1" destination = "172.16.1.10" destination_service = "tcp/9001" } } |
The Terraform file called cisco_asa_terraform.tf is created, and each rule is appended as a resource. This Terraform configuration is still to be tested, but this is the idea currently.
|
0 1 2 3 4 5 6 7 8 9 |
resource "ciscoasa_access_in_rules" "1.1.1.1_172.16.1.10_9001" { interface = "OUTSIDE" rule { source = "1.1.1.1" destination = "172.16.1.10" destination_service = "tcp/9001" } } |
